CYBER SECURITY
ZERO TRUST SECURITY SOLUTIONS
Ensure the security of your organisation at all times with our Zero Trust security model.
Advanced Zero Trust Security for your Business
In response to the ever-changing threat landscape, many organisations are adopting the Zero Trust model as their strategy for security. The Zero Trust security model augments and enhances your technology posture. It effectively adapts to the complexity of contemporary environments and enables organisations to transform security where it is needed.
The model is not about the implementation of individual technologies but rather using technology to enforce the idea that no one has access until they have proven they should be trusted.

We provide a range of zero trust security solutions
We offer consultancy, training, management and ongoing support, to help you identify and mitigate risks and vulnerabilities. We will help guide you through your zero trust security journey.
With information often spread across different cloud providers, it is important to assume that there are attackers both within and outside of the network waiting to strike, and that users or machines should never automatically be trusted.
Identity and Access Management (IAM)
Our IAM solutions offer role-based access control, which lets system administrators regulate access to systems or networks based on the roles of individual users within the enterprise. This is defined according to job, authority and responsibility within the enterprise. They capture and record user login information, manage the enterprise database of user identities, and orchestrate the assignment and removal of access privileges.
Our solutions for IAM include single sign-on systems, two-factor authentication, multi-factor authentication and privileged access management. These technologies also provide the ability to securely store identity and profile data as well as data governance functions to ensure that only data that is necessary and relevant is shared.


Secure Access Service Edge (SASE) Solutions
Our Secure Access Service Edge (SASE) solutions provide mobile users with secure connectivity and consistent security wherever they are in the world. This offers companies a single, centralised view of their entire network.
This allows companies to quickly identify users, devices and endpoints, apply their networking access and security policies, and securely connect users to their applications and data in a cloud or mobile environment.
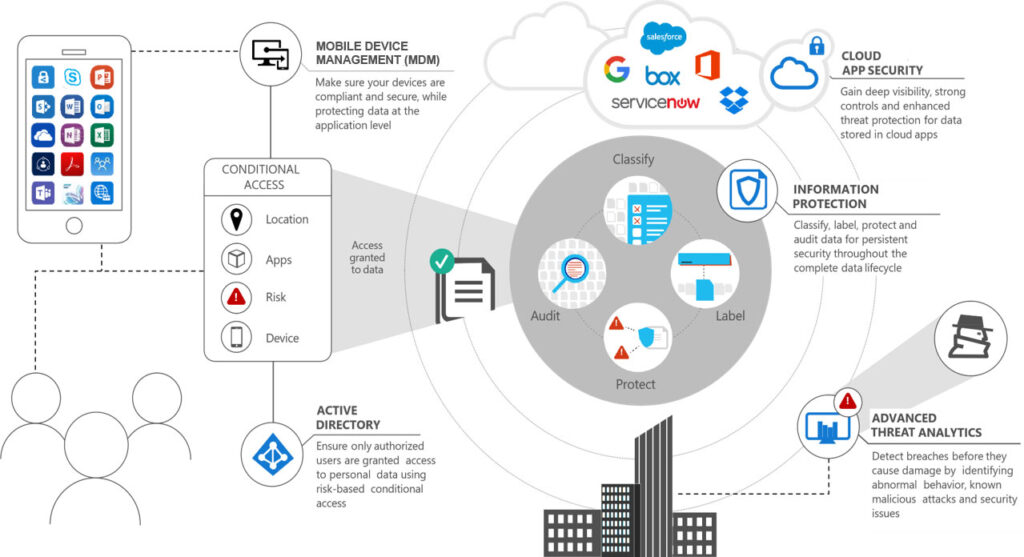
Access management solutions
Our Zero Trust model features a five-stage approach:
- Stage 1 – Define what needs to be protected.
- Stage 2 – Understand how data and systems work
- Stage 3 – Design a Zero Trust security blueprint
- Stage 4 – Create a Zero Trust policy
- Stage 5 – Maintain Zero Trust
Application security solutions
Our application security solutions prevent data or code within an app from being stolen or hijacked. This includes managing hardware, software, and procedures that identify or minimise security vulnerabilities.
Procedures entail things like an application security routine that includes protocols such as regular testing.

Read our live client feedback
Our fully integrated service offering

Frequently Asked Questions - Zero Trust Security
Zero Trust is a security framework that mandates every user, whether within or outside the organisation’s network, to undergo authentication, authorisation, and ongoing validation of security setup and status.
Conventional security models emphasise safeguarding data at the network’s edge, whereas Zero Trust employs end-to-end encryption and data loss prevention methods to ensure data protection at every phase of its existence.
Zero Trust security is a contemporary security approach rooted in the principle of “never trust, always verify.” In contrast to assuming that everything within the corporate firewall is secure, the Zero Trust model starts from the assumption of a breach and scrutinises each request as if it were coming from an unsecured network.

Find out more about how Opus can add value to your business
Reigate Office
London Court
39 London Road
Reigate
Surrey
RH2 9AQ
London Office
60 Cannon Street
London
EC4N 6NP
Hitchin Office
2nd Floor Regal Chambers
49-51 Bancroft
Hitchin
Hertfordshire
SG5 1LL
